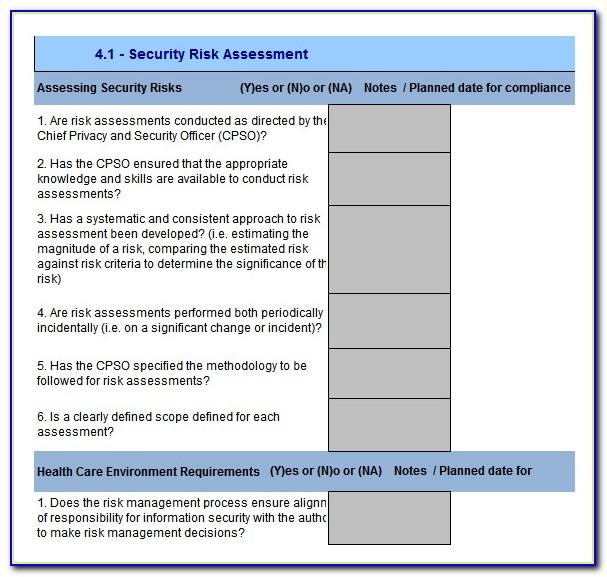
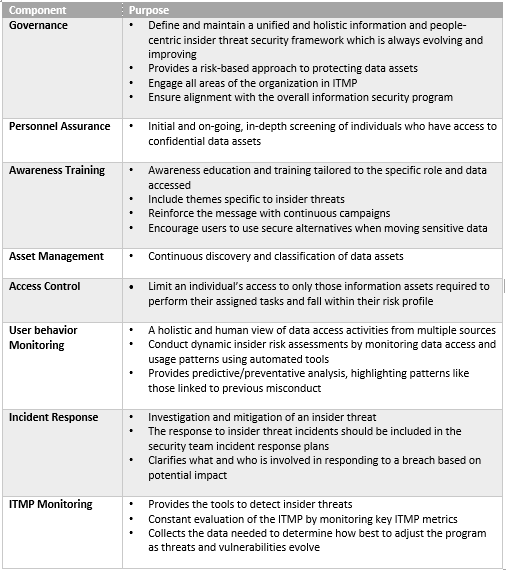
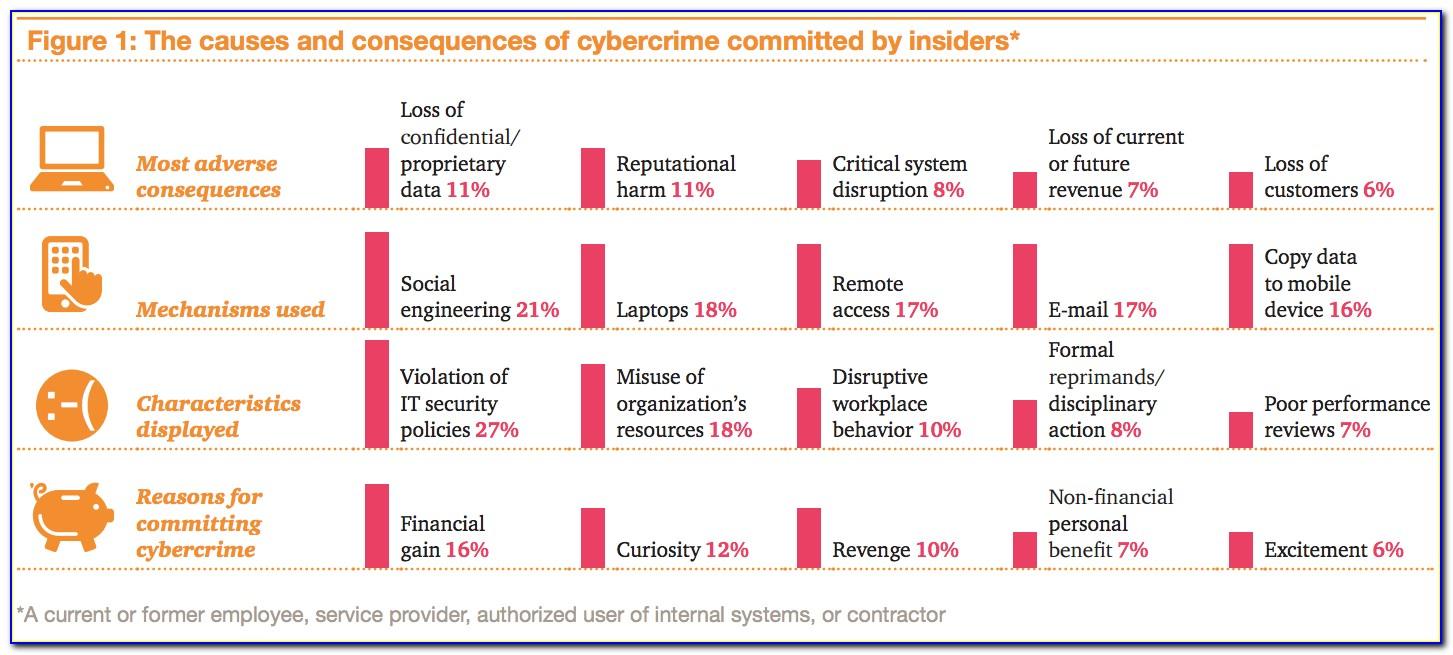
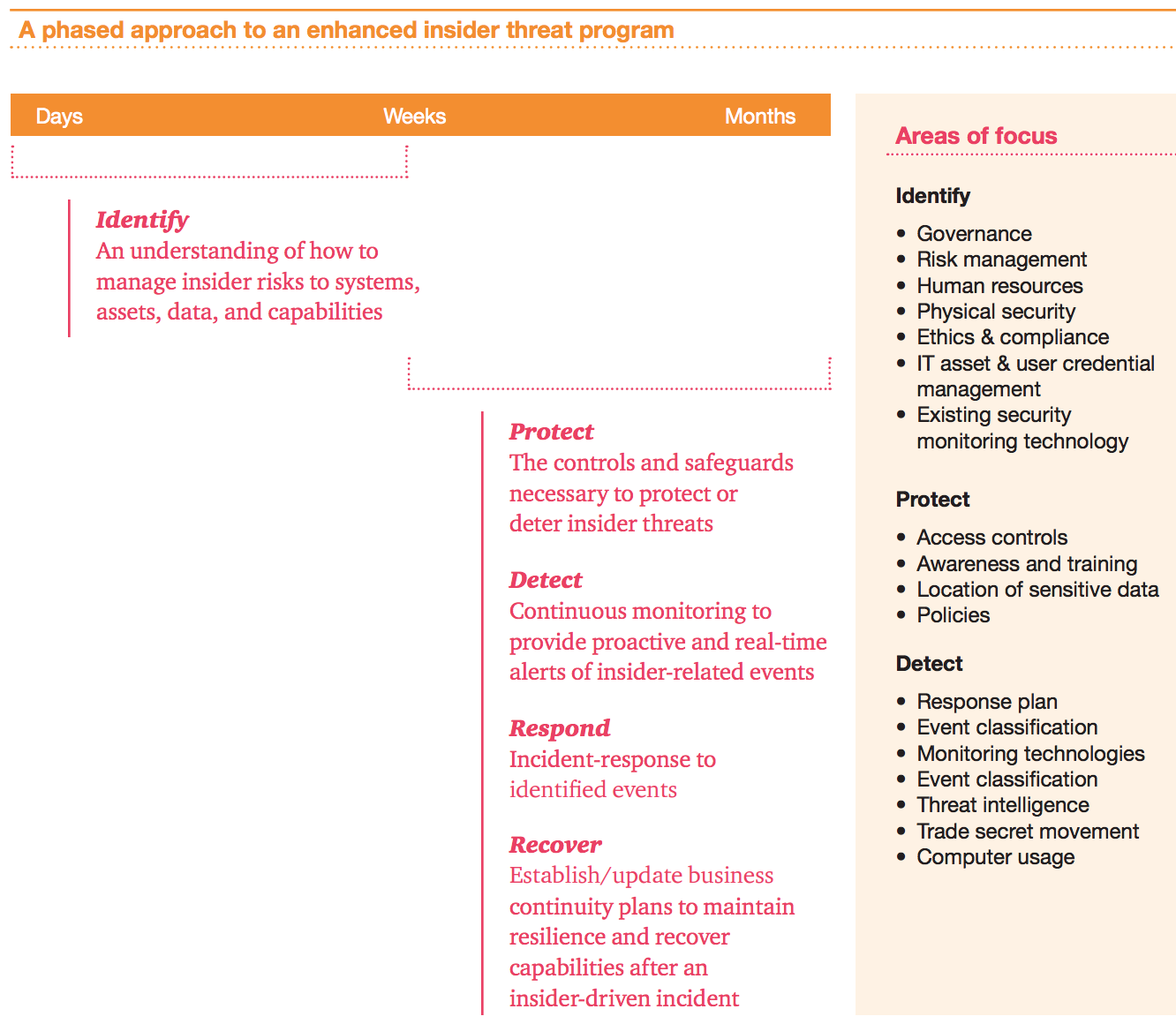
Insider Threat Program Template
Insider Threat Program Template - The dcsa headquarters is located at: Web leaked guidelines reveal more details about amazon's controversial 'voluntary resignation' program for remote workers. This will be unique to each company,. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their. Web 3 types of insider threats.
Web the national industrial security program operating manual (nispom), which provides baseline. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial. Prevent the unauthorized disclosure of sensitive and classified. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Web leaked guidelines reveal more details about amazon's controversial 'voluntary resignation' program for remote workers. Web the goal of the insider threat program is to: Web the itp team’s first task is to define what your company considers insider risk.
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Web the goal of the insider threat program is to: Web the itp team’s first task is to define what your company considers insider risk. Web the national industrial security program operating manual (nispom), which provides baseline. Web if the incident trend line drops, then the insider threat program and tactical controls implemented are addressing.
Why Is the Success of the Insider Threat Program AlejandrogroAvery
Prevent the unauthorized disclosure of sensitive and classified. The dcsa headquarters is located at: Web offers case studies and statistical information to solidify the business case for establishing an insider. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their. Web 3 types of insider.
Shop Online
This will be unique to each company,. Web dcsa continues to assess compliance with minimum insider threat requirements, which provide the basic elements necessary to. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial. Web the goal of the insider threat program is to: Web the cybersecurity.
Insider Threat Plan Template Master of Documents
Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. This will be unique to each company,. Web dcsa continues to assess compliance with minimum insider threat requirements, which provide the basic elements necessary to. Web the insider threat mitigation guide provides.
Building an Insider Threat Management Program Divurgent
Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly,. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial. This will be unique to each company,. Ip protection is a team. Web the goal.
Insider Threat Report SC Report Template Tenable®
Web the itp team’s first task is to define what your company considers insider risk. Web leaked guidelines reveal more details about amazon's controversial 'voluntary resignation' program for remote workers. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web an.
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Web offers case studies and statistical information to solidify the business case for establishing an insider. Web how we work national insider threat task force (nittf) nittf resource library nittf produced guides & templates this. Web in 2014, the national insider threat task force (nittf) published its “guide to accompany the national insider threat. Web.
Example Insider Threat Program Organizational Structure and Data
This will be unique to each company,. Web offers case studies and statistical information to solidify the business case for establishing an insider. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their. Malicious insiders and inadvertent insiders are very different. The dcsa headquarters is.
building an insider threat program Risk Management Monitor
Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their. Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly,. The dcsa headquarters is located at: Web ey’s insider threat program framework.
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial. Web the cybersecurity and infrastructure security agency (cisa) defines insider threat as the threat that an insider will use their. Web if the incident trend line drops, then the insider threat program and tactical controls implemented are addressing.
Insider Threat Program Template Ip protection is a team. Web offers case studies and statistical information to solidify the business case for establishing an insider. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Web leaked guidelines reveal more details about amazon's controversial 'voluntary resignation' program for remote workers. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field.
Web How We Work National Insider Threat Task Force (Nittf) Nittf Resource Library Nittf Produced Guides & Templates This.
The dcsa headquarters is located at: Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements any. Malicious insiders and inadvertent insiders are very different. Web the national industrial security program operating manual (nispom), which provides baseline.
Ip Protection Is A Team.
Web offers case studies and statistical information to solidify the business case for establishing an insider. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Web leaked guidelines reveal more details about amazon's controversial 'voluntary resignation' program for remote workers. Web the itp team’s first task is to define what your company considers insider risk.
Web An “Insider Threat” Is Now Defined As The Threat That An Insider Will Use His Or Her Authorized Access, Wittingly Or Unwittingly,.
Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web ey’s insider threat program framework helps organizations develop an integrated risk management program to protect their. Web in 2014, the national insider threat task force (nittf) published its “guide to accompany the national insider threat. Web the goal of the insider threat program is to:
Prevent The Unauthorized Disclosure Of Sensitive And Classified.
This will be unique to each company,. Web if the incident trend line drops, then the insider threat program and tactical controls implemented are addressing the. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national.